Configuring Cognos Single Sign-on with Multiple Authentication Providers
During the course of an IBM Cognos environment’s lifespan, there may be times when you will need to configure IBM Cognos to allow users to connect to more than one third party authentication source from the same Cognos portal. This can happen in several scenarios.
One scenario can occur during a migration from a previous Cognos version. Example: Access Manager may have been used to secure IBM PowerCubes; however, the original Transformer models or original data sets are no longer available to rebuild the cubes. You may not be able to re-develop the embedded security views in Cognos 10 due to the source data changing or for other reasons.
Another example may occur when 2 or more environments are being merged to the same IBM Cognos platform, but corporate IT requirements dictate keeping the existing security providers for separate business applications. Or, perhaps another system with built-in security is used for some content, such as SAP BW.
This article will walk through the steps necessary for enabling 2 authentication providers using the single sign-on (SSO) option without prompting users for authentication to either namespace.
Note: This example requires IBM Cognos 10.1.1 BI Server Fix Pack 1 (FP1) or higher (10.1.6301.14).
Scenario
An existing IBM Cognos 10.1.1 FP1 installation has Active Directory already configured for SSO as the only namespace. A business application group wants to migrate from series 7 with PowerCubes that have embedded custom views secured against Access Manager. Access Manager is installed on a separate server and is set up for OS authentication with single sign-on. The content manager and report server are on the same machine and the gateway is on a separate machine.
On each application server, launch Cognos Configuration. Our first step is to stop the Cognos services on all application-tier components. Stopping and starting is always required with any security namespace change.
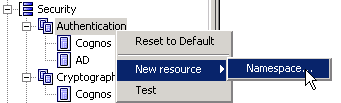
Under the Security node, right-click on Authentication, select New Resource > Namespace:
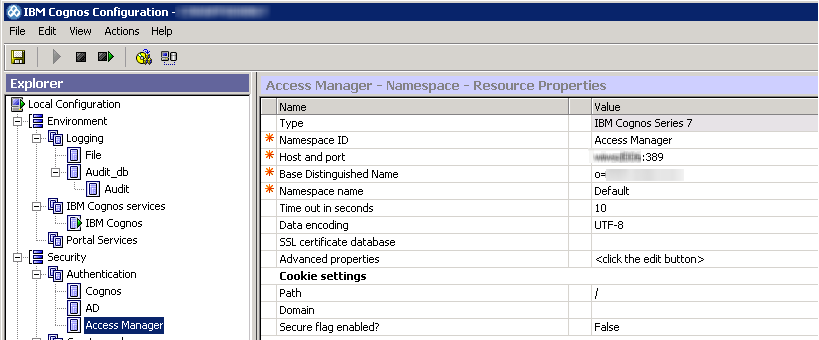
Configure this namespace according to your own settings. We’ll choose IBM Cognos Series 7 and name it Access Manager. Note this is the Namespace ID, not the name. This is the ID that will be stored in the content store and will be displayed in the Security tab of the Cognos Connection Administration console once enabled:
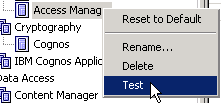
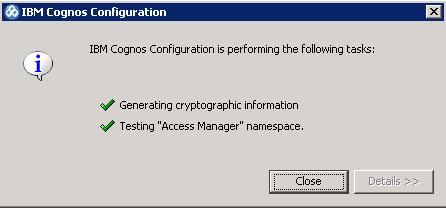
Test the namespace:
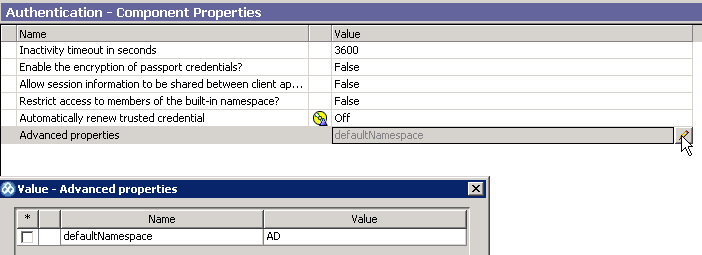
Next, select the Authentication node and select Advanced Properties. Add a new entry called defaultNamespace and give it a value of AD (this is the Namespace ID previously created for Active Directory). The reason for this step is to force the Cognos gateway component to attempt authentication to the AD namespace first since it is the most commonly used authentication provider for most of our reports.
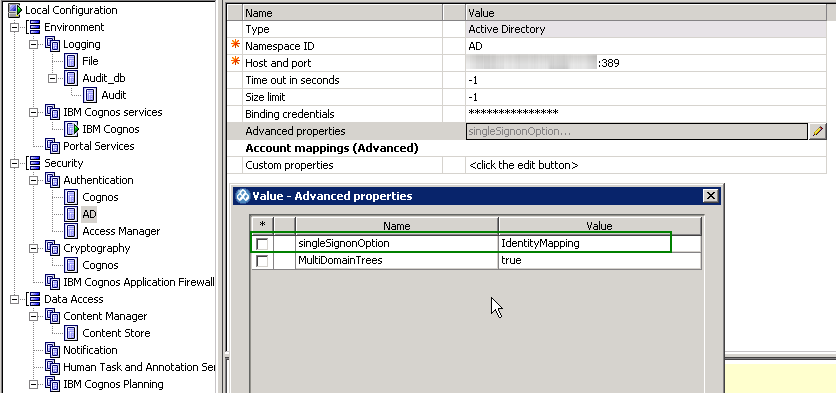
Note also that at the AD sub-node, the Advanced properties shows singleSignonOption with a value of IdentityMapping. This is required to enable single sign-on for AD and should have been set up previously (as mentioned earlier).
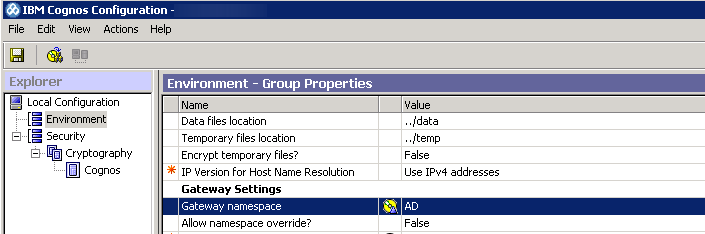
Next, let’s look at Cognos Configuration on the gateway machine. Note that the Gateway namespace is currently set up as AD:
We want to remove this and keep this value empty. Note that if we do not do this, the Access Manager namespace will be ignored since the gateway can only point to one default namespace.
Next, save the gateway configuration.
Lastly, go back to the application server(s), save the configuration and start up the service(s).
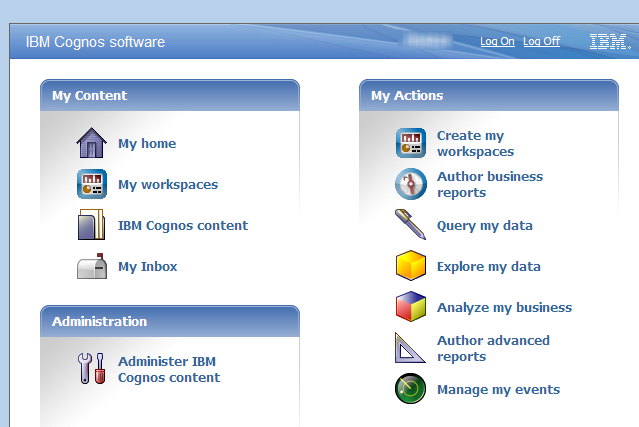
Next, open a browser and go to your IBM Cognos URL. You are now logged on to the AD namespace using single sign-on:
Note the Log On link above, indicating that there are other namespaces available to this IBM Cognos environment. Click the Log On button:
You’ll see that the Log On link no longer appears, indicating the user is now authenticated to all available namespaces.
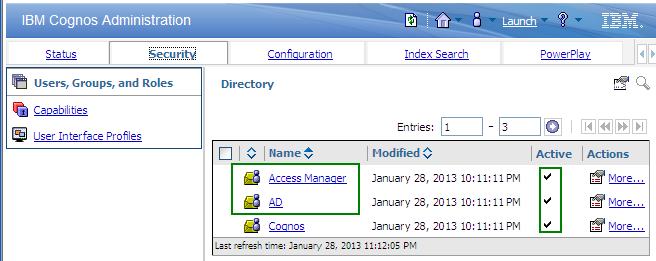
If you are an administrator, you can see that there are 2 authentication namespaces associated to this Cognos environment. Go to the Security tab of the Administration console:
To further prove that this user can now authenticate to both providers, you may want to publish an Access Manager secured cube to Cognos Connection to try to gain access to it.
Conclusion
As you can see, adding multiple authentication providers using SSO is a fairly straightforward task in IBM Cognos 10.1.1 FP1 or higher. Hopefully this will provide some insight into this technique and give you flexibility not previously possible in older Cognos versions.